Long-range IoT networks constitute the foundations of a low-power wide area network (LPWAN). In these networks, end nodes in the form of devices that have low power consumption are connected to gateways that, in turn, transmit data to other devices and network servers. Devices on the network then analyze the data that is received and control the devices at the end nodes accordingly.
The two most popular technologies for LPWAN are Sigfox and LoRaWAN. However, for this book, we will discuss LoRa in more depth as opposed to Sigfox, given that it is based on an open standard, provides the capability of building both private and public networks – with tens of thousands of networks already established in the world – and has a lower data rate compared to Zigbee.
The following diagram shows the four different data layers of LoRa. Can you see how it differs compared to the layers that were illustrated for Zigbee? Why and how does this affect its use?
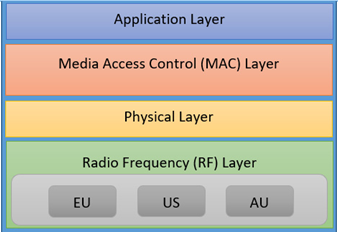
Figure 4.1 – Data layers of LoRa
The radio frequency (RF) layer works with RF assignment and helps transmit baseband information through an RF carrier through an antenna over the air. As can be seen, different frequency bands within the RF layer are allocated for the different regions of the world. For simplicity, we have omitted the numerical band identifier and instead just illustrated it with the initials of the region. The physical layer is above RF and helps with header formation, preamble, and the header’s CRC. The raw data that is provided by the frame is then modulated with LoRa CSS/FSK or GFSK before RF conversion is done for uplink transmission. The layer also supports RF issues relating to interference, coverage, and optimization. The MAC layer helps assist with MAC management messages between a server and an end device. MAC takes care of functions such as energy consumption, mesh topology, and security. The application layer is the topmost layer and is designed to be used based on the specific use case of the user, such as with smart cities, smart grids, healthcare, and many more.
While both LoRaWAN and Zigbee are significant technologies within the realm of IoT networking, they cater to different use cases due to their distinct networking topologies and capabilities. LoRaWAN, with its long-range communication abilities, operates in a star-of-stars topology, making it well suited for urban and wide-area deployments. Conversely, Zigbee, with its short-range communication abilities, operates in a mesh topology, which is ideal for more compact, localized networks.
Now, let’s delve into the structure of LoRaWAN while highlighting a deployment in an urban area where LoRaWAN’s long-range communication capability shines. Figure 4.2 demonstrates how such a setup might be structured:
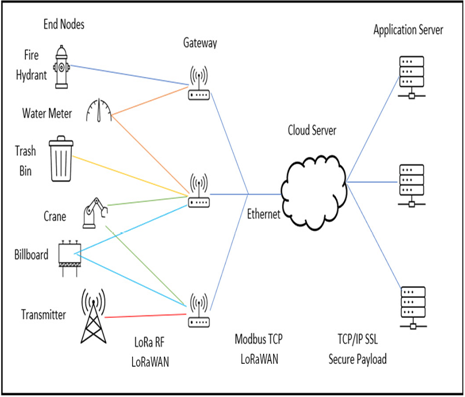
Figure 4.2 – Sample structure for the LoRa network
Within this setup, we can see that the sensors are positioned as end nodes at smart objects that are located around the urban area, including a fire hydrant, a billboard, and a transmitter. As can be surmised, these are objects that would be lying hundreds of meters – if not kilometers – from each other, making the choice of a long-distance protocol over a short-distance protocol imperative. We can see that everything connects to a specific gateway that it is assigned to, with some end node types connecting to multiple gateways while some types only connect to one. This data transmission is done through LoRa RF LoRaWAN, allowing data to be transmitted through RFs that are the defaults within LoRa networks.
The gateways are then connected to the cloud server via Ethernet, utilizing standard TCP/IP or UDP/IP protocols for the backhaul communication. This setup allows for reliable data transmission from the local network of sensors to the cloud infrastructure. Once the data reaches the cloud server, it is forwarded to the application server. This arrangement enables users to access the collected data and, if necessary, send data back to the cloud server for further processing or control operations. The communication between the cloud server and the application server, as well as between the users and the servers, can be secured using SSL/TLS protocols over TCP/IP, ensuring data integrity and confidentiality during transmission.
The network architecture, as depicted here, considers the appropriate protocols for transmitting data between devices, gateways, and servers, while also addressing the security concerns inherent in each data transmission stage. Ensuring a secure and reliable data communication framework is crucial. We’ll delve into this aspect in more detail in Chapter 11, Examining Security and Privacy in IoT.

